Infographic How to Strengthen the Military’s Cybersecurity Posture Using Zero Trust Tools with Insight Public Sector
By Insight Editor / 6 Dec 2023
By Insight Editor / 6 Dec 2023
The path to a future-proof, threat-protected military IT environment requires relentless strategic attention to both future and present defenses, as well as the right technology. Military entities looking to adopt Zero Trust cybersecurity tools and best practices can use the following checklist as their guide. Consult with an Insight Public Sector expert for an in-depth assessment.
Accessibility note: The infographic is transcribed below the graphic.
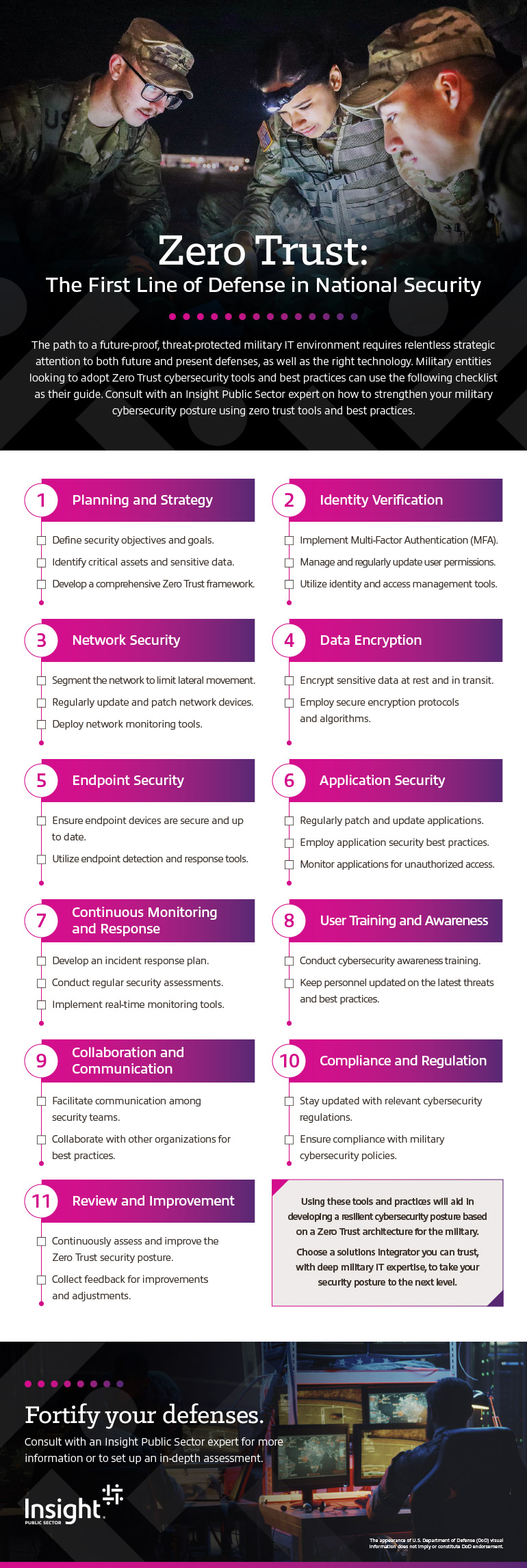
Infographic text included for screen readers:
The path to a future-proof, threat protected military IT environment requires relentless strategic attention to both future and present defenses, as well as the right technology. Military entities looking to adopt Zero Trust cybersecurity tools and best practices can use the following checklist as their guide. Consult with an Insight Public Sector expert for an in-depth assessment.
1. Planning and Strategy:
2. Identity Verification:
3. Network Security:
4. Data Encryption:
5. Endpoint Security:
6. Application Security:
7. Continuous Monitoring and Response:
8. User Training and Awareness:
9. Collaboration and Communication:
10. Compliance and Regulation:
11. Review and Improvement:
Using these tools and practices will aid in developing a resilient cybersecurity posture based on a Zero Trust architecture for the military.
Choose a solutions integrator you can trust, with deep military IT expertise, to take your security posture to the next level.